2 min read
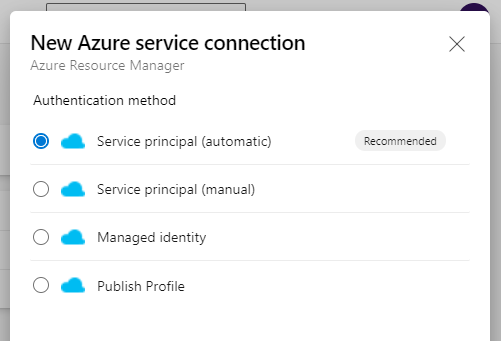
Create an Automatic Service Principal Azure RM Service Connection in Azure DevOps via Azure CLI
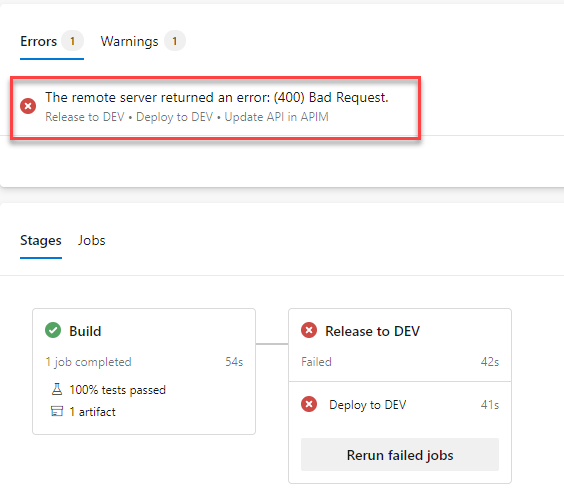
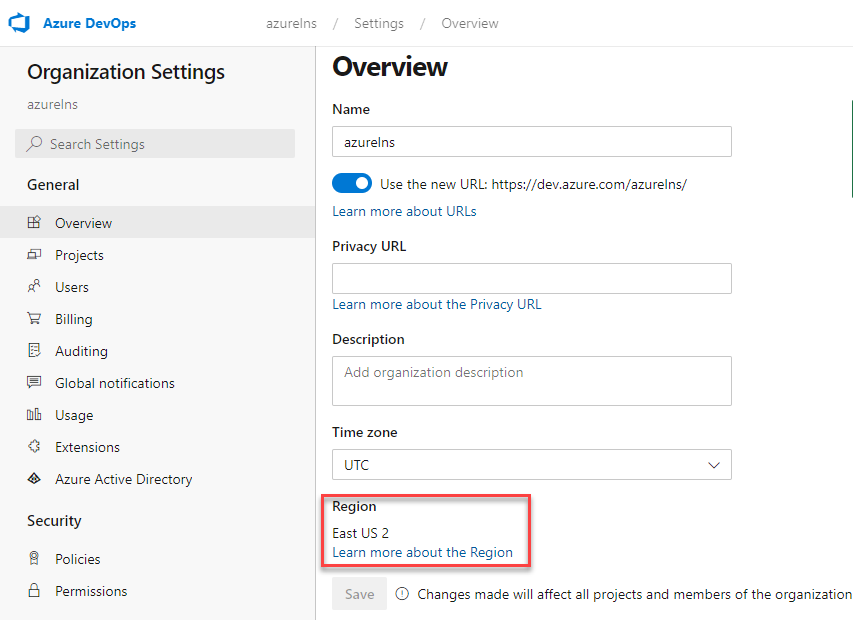
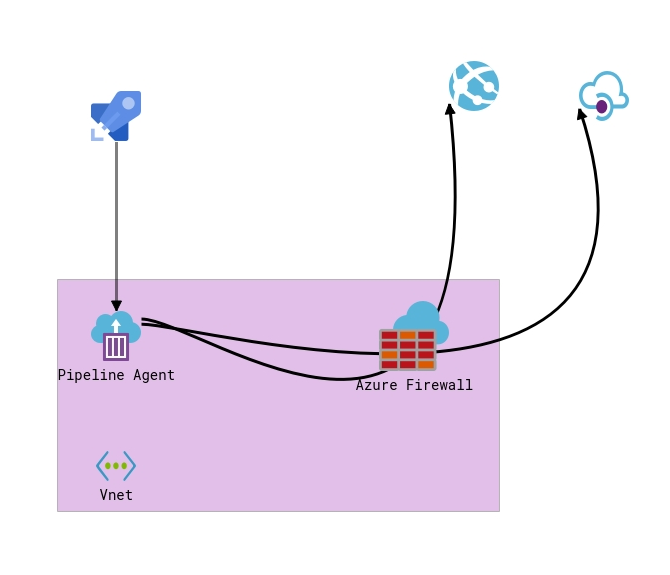
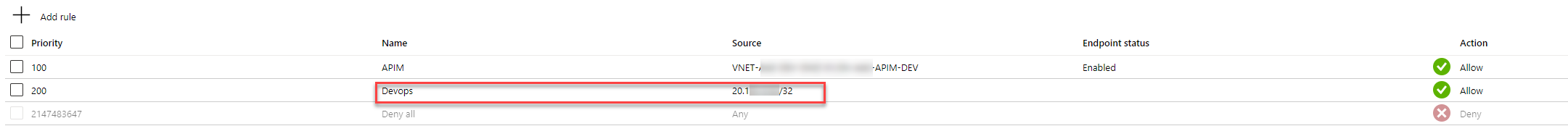
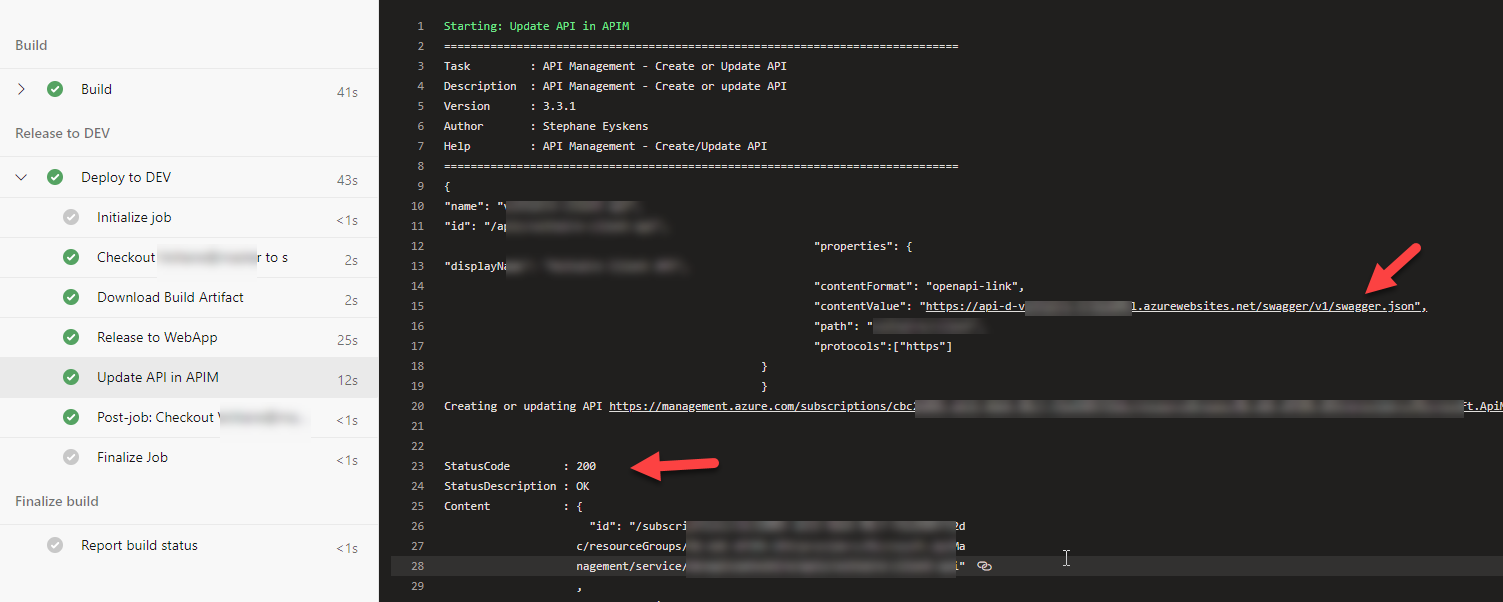
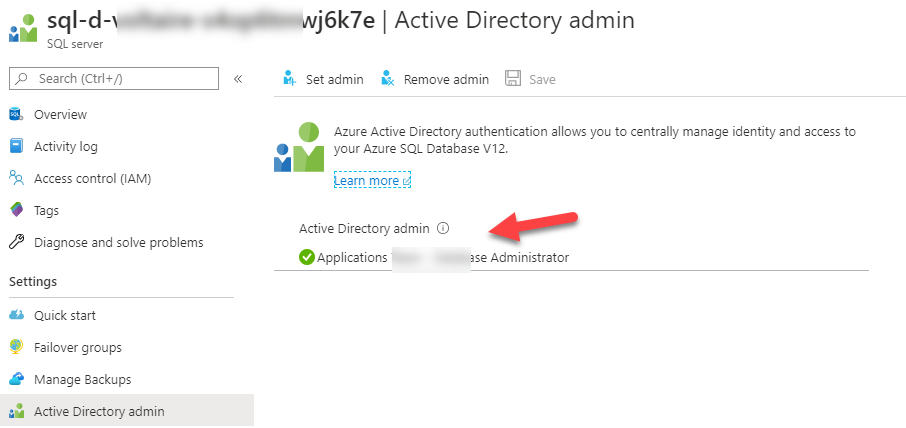
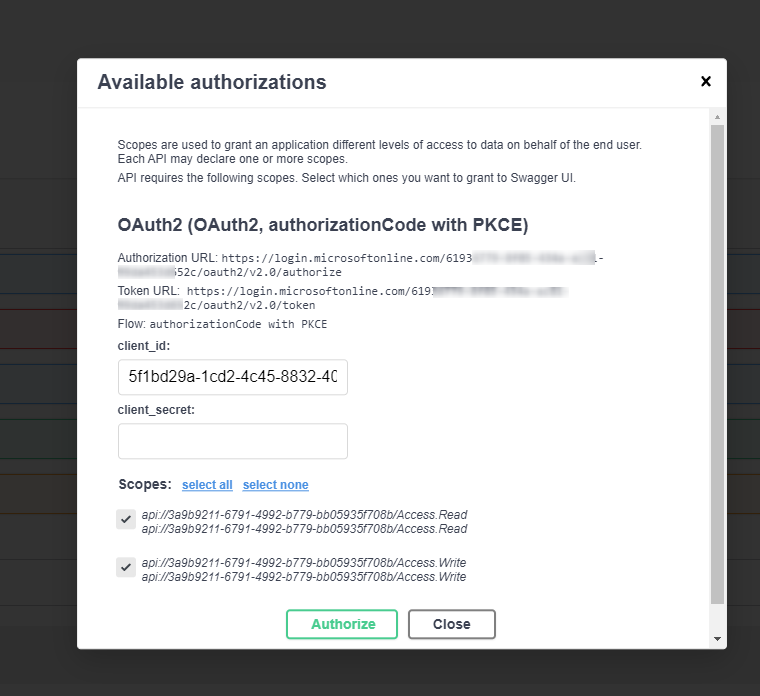
With more and more of our development and infrastructure projects being built and released via Azure DevOps, I find myself creating a few DevOps...