2 min read
Enable Azure AD authentication for API Management Service Developer Portal
We use Azure Api Management Service (APIM) quite a lot and recently I have been looking at the new APIM Developer portal and how to enable Azure...
2 min read
Alexandre Verkinderen : Dec 8, 2023 1:32:00 PM
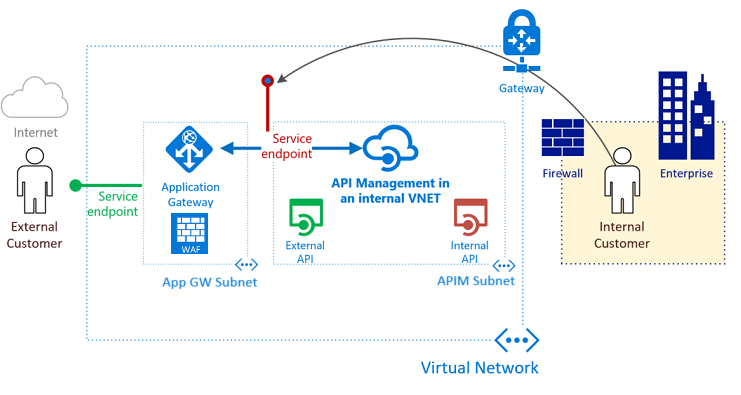
There are currently 2 developer portals for the Azure API Management service: a legacy portal and the new portal experience. We deployed our Azure APIM instance before the new portal was released so we were still running on the legacy portal. We are running our Azure APIM instance with custom domains on an internal vnet behind an application gateway with WAF and the default OWASP 3.0 rules enabled. This appeared to be a real challenge with the new developer portal.
In this blogpost I will cover how to move to the new developer portal experience and changes that are required on your Application Gateway.
If we want to use the new developer portal we need to publish a new APIM management endpoint and create a new CNAME in our publis DNS register. The old developer portal only requires the portal endpoint to be published as shown below:
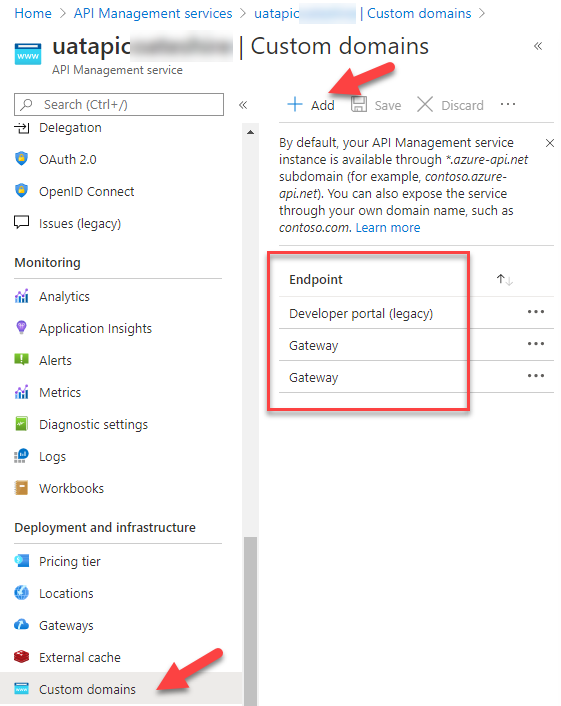
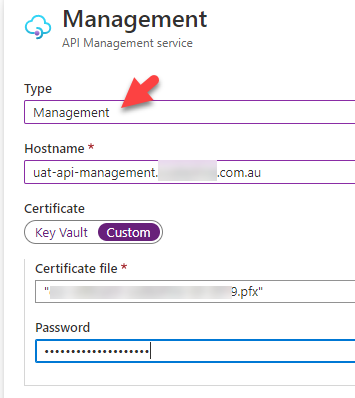
To add the new management endpoint click custom domains and add new. Select Management and provide your custom hostname and certificate.
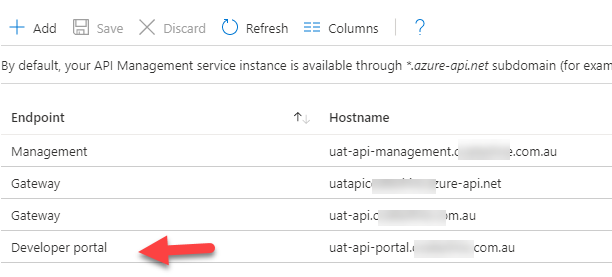
Next, we will add the new developer portal with a custom domain and remove the legacy developer portal custom domain. Your custom domains should look like this:
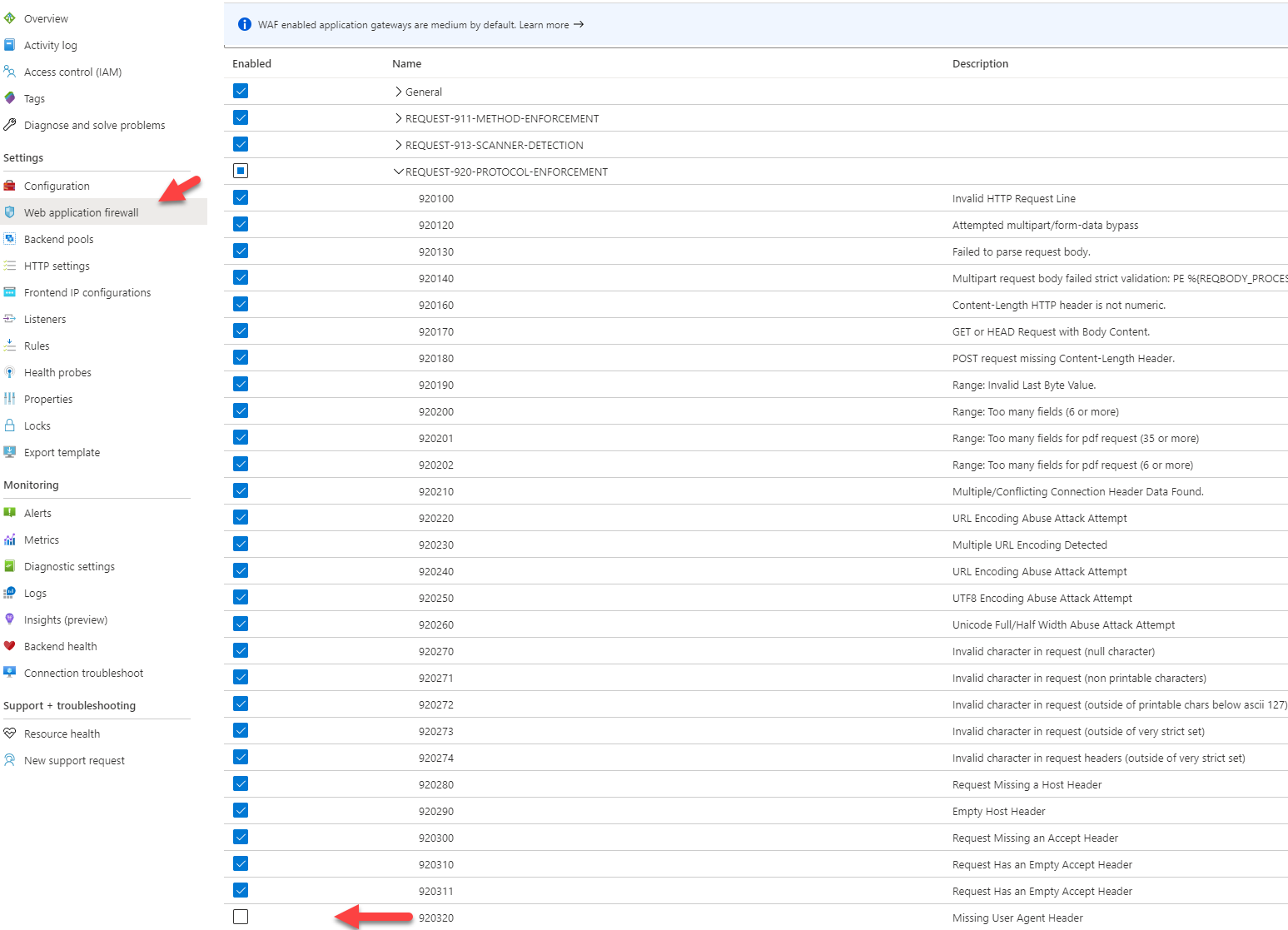
I have my Azure APIM sitting on a virtual network behind an Azure Application gateway. The legacy portal is fully comptabile with WAF OWASP 3.0 rules. However, as of writing this article, the new Azure APIM developer portal is not fully compatible with the industry standard OWASP rules. The WAF will block certain requests and treat them as SQL injections for example. Luckily my WAF and App gateway are only used for this APIM so I could lower my security, as a workaround, and disable certain rules. But I can imagine you would not be so happy to disable those rules if all your traffic is going through the same app gateway. The following rules are to be disabled:
Next, as we have a new endpoint, we need to update our health probes and app gateway settings. Go to your Azure Application Gateway and configure the listener and rules like this:
Create a new Health Probe
Add the new management endpoint public address the host.
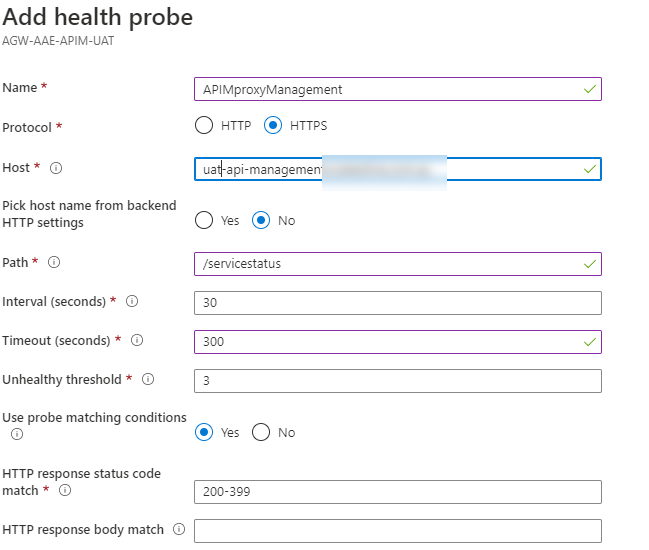
Notice that we used /servicestatus for the path.
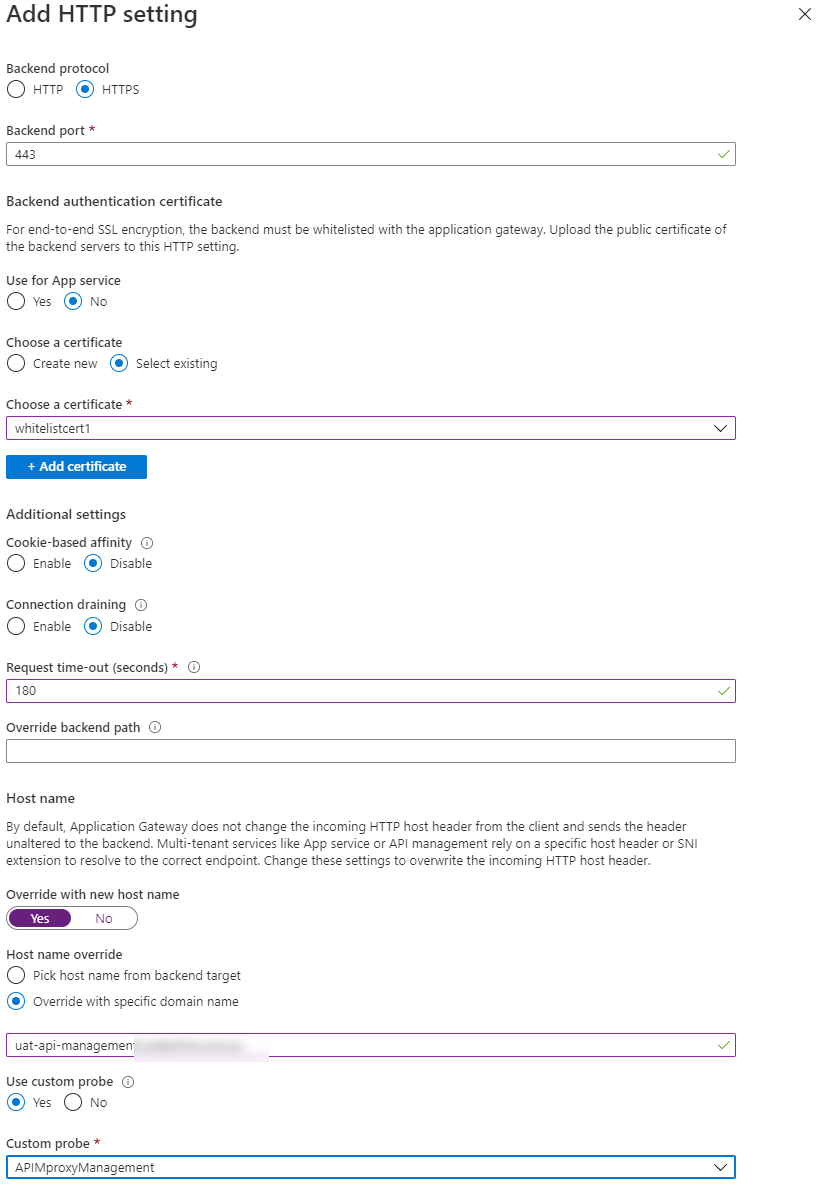
Create new HTTP Settings:
Add the following new HTTP setting to include the new management endpoint:
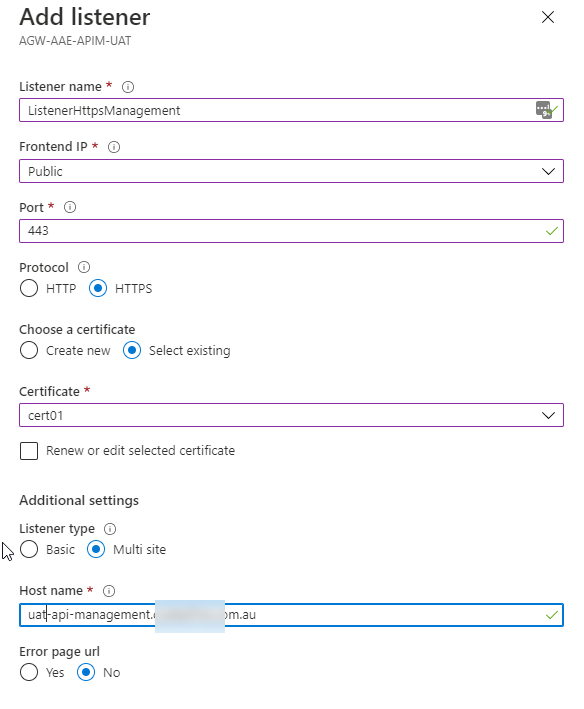
You will need to add 2 new listeners:
You wil need to create 2 listeners. One for the management endpoint on https on port 3443 and one for https on port 443:
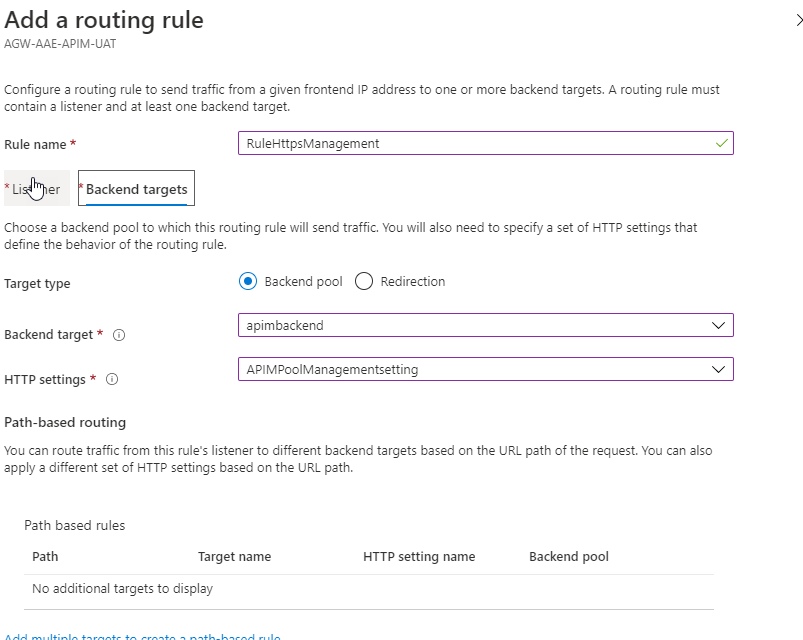
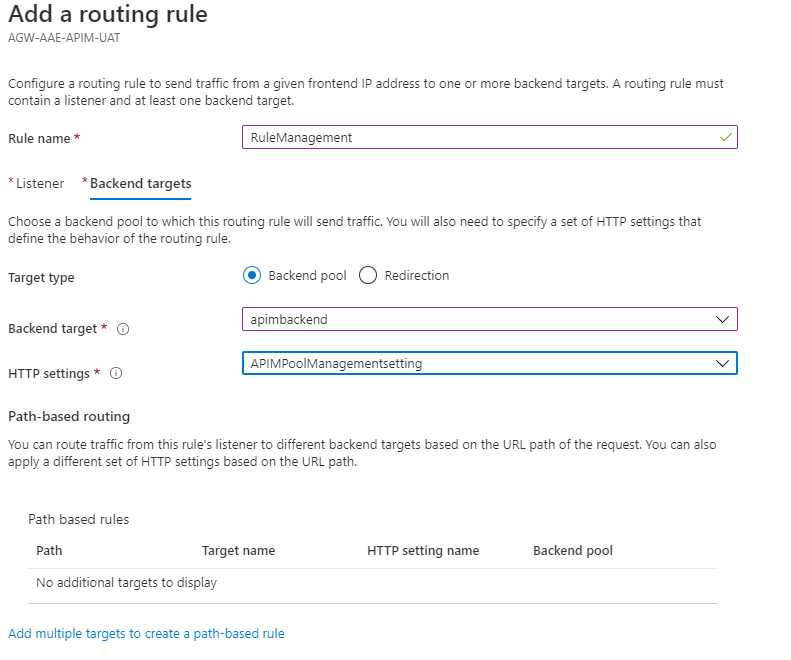
You will also need to add 2 new routing rules:
Create 2 new routing rules for:
That’s it for the application gateway.
The new developer portal was not provisioned correctly in my environment. I had a blank screen when I checked if it was working properly. After logging a call with MS support they told me I had to reprovision the new developer portal. I guess that’s due to the WAF rules blocking certain requests and the new portal was not properly provisioned. To provision the new portal you will need a script that you can find here. It will require node js to be installed.
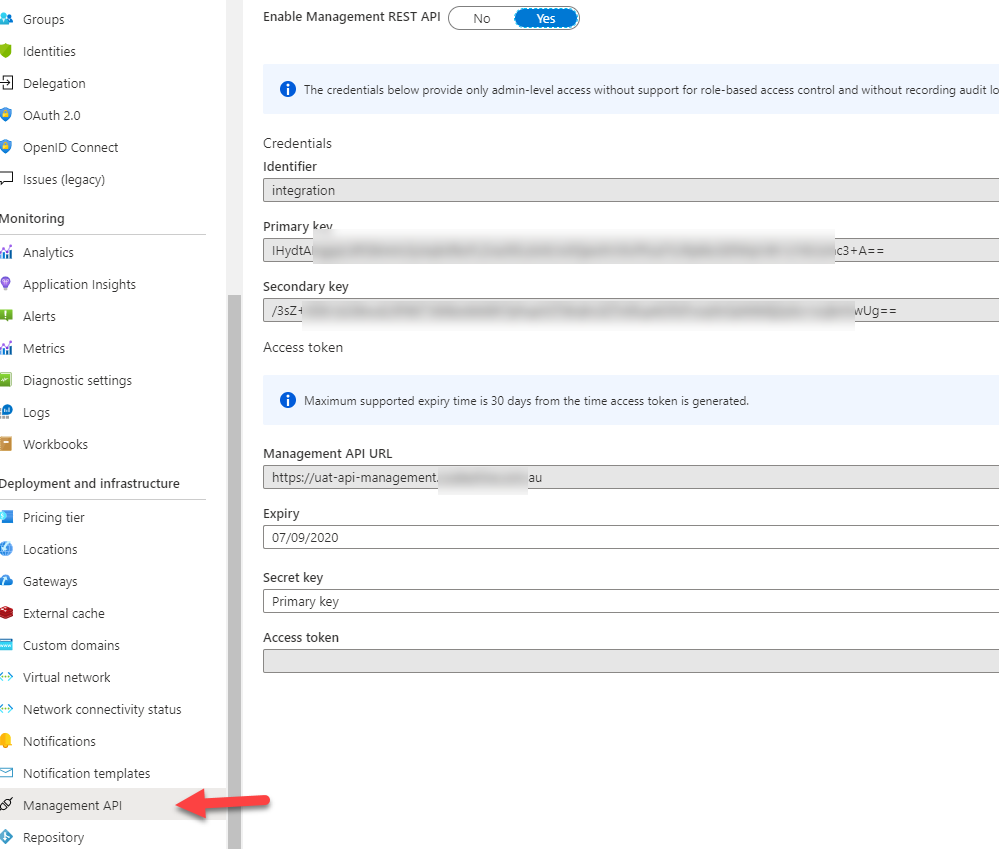
For the script to execute you need a management API key. Go to your API management instance and in ‘Management API ‘ click enable and generate to get the Shared access signature token.
Open the generate-data.bat file and fill in your shared access key and update the management endpoint:

Run the bat file from the command prompt. This will provision the new API developer portal experience.
Hope this helps,
Alex
2 min read
We use Azure Api Management Service (APIM) quite a lot and recently I have been looking at the new APIM Developer portal and how to enable Azure...
1 min read
Microsoft has announced a new Azure API Management Consumption tier. This new tier aligns with serverless architecture principles that includes...
3 min read
By default, when you deploy a new Azure WebApp, Function app or API app it will be publicly available to the internet. For the current customer I’m...