2 min read
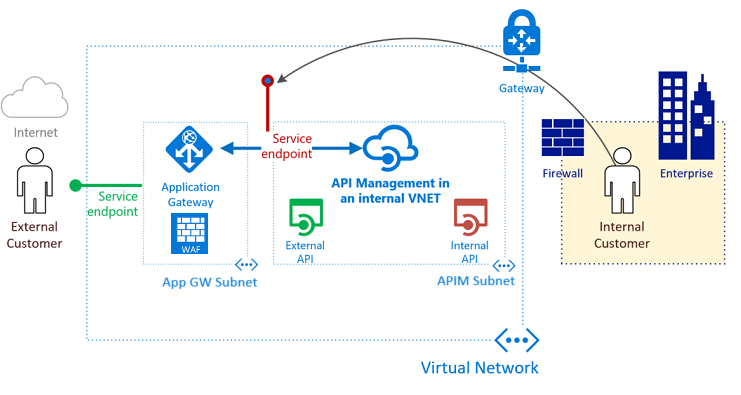
Publish the new Azure API Management Service Developer Portal behind an Application Gateway
There are currently 2 developer portals for the Azure API Management service: a legacy portal and the new portal experience. We deployed our Azure...